By Blerim Abedini, Institute for Security Studies and Development, ISSD-NM
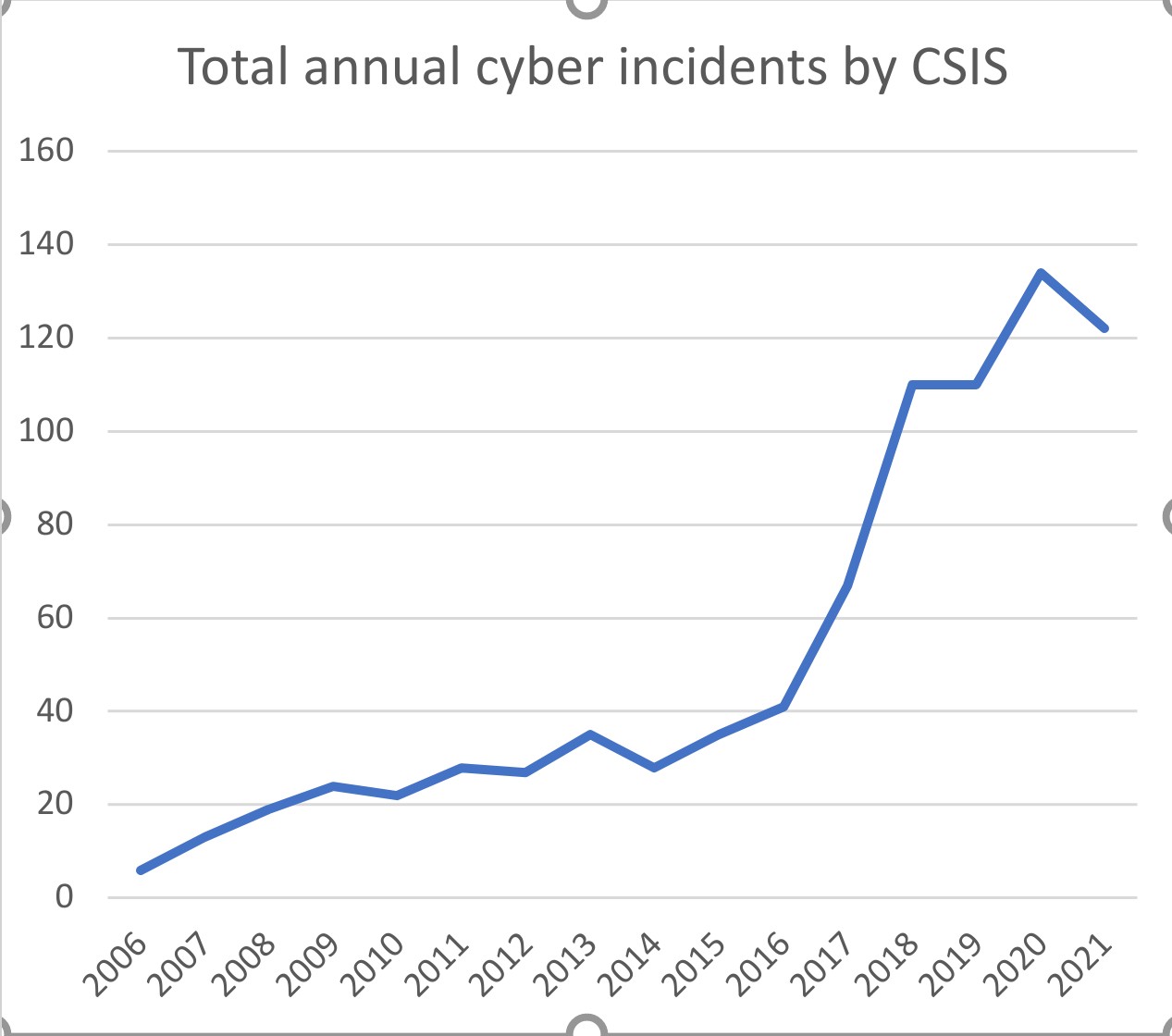
The chronology of events recorded by the Center for Strategic and International Studies (CSIS) in Washington reflects the fragile political relations left over from the Cold War, continuing with hybrid warfare, such as the cyber incidents studied from 2006 against government agencies, department of defense and economic fraud with losses in several million dollars.
A total of 12 cyber incidents were recorded in June 2022, reported by FBI, National Security Agency (NSA), and CISA (Cyber Security and Infrastructure Security Agency). In this case, Chinese state-sponsored hackers have attacked major telecommunications companies with network services since 2020 in the US. While there has been no shortage of counterattacks by hackers revealing archives and photos known as “Xinjiang Police Files” that show human rights violations against the Uyghur population.
Seven incidents were recorded in May 2022. Most notably, state-sponsored hackers (believed to be Ukrainian) took down RuTube, which is the Russian version of YouTube (https://youtu.be/bmEduJePgXk).
16 incidents were recorded in April 2022. During actions, the United States has removed Russian malware from computer networks around the world. Authorities have clarified that this software can be used for surveillance and destructive attacks. The malware was launched by the Russian GRU (General Staff of the Armed Forces of the Russian Federation).
12 incidents were recorded in March 2022. The attack was on a satellite (its modems), which was operated by the American company Viasat. On this occasion, internet services in Europe have been interrupted. It also included Ukrainian military communications prior to the Russian invasion. This Russian attack was followed by a counterattack by hackers who broke into websites in Russia, belonging to multiple Russian agencies, including the Ministry of Energy, the Federal State Statistics Service, the Federal Penitentiary Service and the Federal Enforcement Service of Russia. Images and messages against the invasion of Ukraine appeared on websites. In March of this year, it was also reported by the China Computer Network Emergency Technical Team/Coordination Center (CNCERT/CC) that hackers from the United States had manipulated Chinese computers to carry out indirect attacks in Russia, Ukraine, and Belarus.
13 incidents were recorded in February 2022. The most impressive are campaigns by two groups that have been supported by the North Korean government, that attacked employees in media, fintech, and software companies. Hackers have used phishing e-mails for fake ads, using Google Chrome to decompress websites and spread malware software. In the same month, a Beijing-based cyber security company accused the US National Security Agency of creating a ‘backdoor’ to monitor companies and governments in over 45 countries around the world. The Foreign Ministry spokesman has declared that this operation could threaten the security of China’s critical infrastructure and compromise its trade secrets. Also in the same month, a UN report announced that North Korean hackers have stolen more than $50 million between 2020 and 2021 from three cryptocurrency exchanges. The report says that in 2021 attacks have increased 7 times, on cryptocurrency platforms aimed at helping to finance the nuclear program of the North Korean regime because of international economic sanctions.
Also, 10 incidents were recorded in January 2022. By, the most characteristic is the shutdown of North Korea’s Internet traffic twice for two weeks which resembled a series of DDoS attacks. The attacks were the reason for North Korea’s fifth launched missile test. Also this month, the IT Directorate of the Greek Parliament has identified efforts to open 60 electronic communication accounts of the Greek Parliament. In response, the Greek authorities have temporarily shut down its communication network.
In addition to these, we are witnessing cyber attacks in the Balkans. But these incidents are considered secondary since the state strategy as well as the funding of these state security agencies, does not promise a stable defense strategy against cyber attacks. We are witnesses to the attack in Albania on July 18, 2022, which was a cybercriminal attack synchronized from abroad in the announcement of the Council of Ministers but without finding the country of origin. We are also reminded of the 2020 cyber-attack on the parliamentary elections in North Macedonia, with a DDoS attack on the website of the country’s election commission which passed without the attacker being detected.
In 2020 hackers targeted the public administration of the northern Serbian city- Novi Sad, demanding around 400,000 euros. In May 2020, a group of Greek hackers called “The Mighty Greek Army” opened dozens of emails and passwords of employees in the Ministry of Finance and Economy of North Macedonia as well as in the municipality of Strumica. Also, according to Montenegro’s defense ministry, the defense systems have detected and prevented over 7,600 malware threats and more than 50 attempted phishing attacks during 2020 and 2021.
We may conclude that the developed states within governments and companies are paying appropriate insurance agencies to maintain the defense system, health, licensed technologies, communication media, non-government organizations, companies with thousands of employees, government secret files, state administration staff, officials, police and other fields that are strategic for a modern state.
Comments are closed, but trackbacks and pingbacks are open.